CISV takes the privacy of our participants and volunteers seriously and we strive to ensure good Data Protection practices in all parts of our organization.
CISV International makes continual efforts to respect your privacy and to be clear with you about the type of data we will need from you, how we will use it, and for what reasons. We know how important your privacy is to you and we work with our volunteers, staff, and host families around the world to keep your information as safe and confidential as possible.
We have developed several resources to assist our National Associations, Chapters, and Volunteers in ensuring good Data Protection everywhere.
First among these is our Data Protection Miniguide. This document summarises and explains CISV’s approach to Data Protection. This approach is based on the General Data Protection Regulation (GDPR) from the European Union.
Secondly, we have the Data Protection and CISV Forms document which details how we gather, use, store, destroy and archive the data we collect in the forms related to our international programmes. This document is particularly useful to the staff, leaders and local contact persons for our programmes.
Thirdly, we have the Data Privacy Notice Regarding Participation in CISV International Programmes which all of our National Associations and Chapters can use and adapt to their own local and national laws, to inform our participants, parents and volunteers why we need their data and what we do with the data.
For those involved with the technical side of Data Protection, we have included a few relevant questions and answers below.
Data Protection FAQs
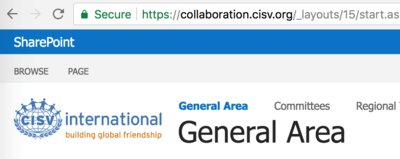 TLS – or transport layer security – is a protocol for data and/or files that travels between your computer and an internet server. It was formerly called "SSL" (secure socket layer). Both terms refer to the fact that the data travelling between computers in the internet is encrypted. You can identify a website’s use of this protocol – and therefore a website using encryption – by looking at the little "s" before the colon in your browser’s address line (e.g. https://collaboration.cisv.org). This not only applies to CISV websites but to everything you do on the internet. If data travelling from your computer to the webserver is being encrypted, hackers who manage to catch your data are not easily able to actually read and use it.
TLS – or transport layer security – is a protocol for data and/or files that travels between your computer and an internet server. It was formerly called "SSL" (secure socket layer). Both terms refer to the fact that the data travelling between computers in the internet is encrypted. You can identify a website’s use of this protocol – and therefore a website using encryption – by looking at the little "s" before the colon in your browser’s address line (e.g. https://collaboration.cisv.org). This not only applies to CISV websites but to everything you do on the internet. If data travelling from your computer to the webserver is being encrypted, hackers who manage to catch your data are not easily able to actually read and use it.